SOLIDWORKS: Choosing and Configuring a SOLIDWORKS PDM Pro Login Type
Windows Login for PDM
Objective
Assist SOLIDWORKS PDM Professional Customers when choosing a Login Type and provide information required for Windows Active Directory setup and functionality. For PDM Standard, there is no choice for Windows Login currently available.
Definitions
SOLIDWORKS PDM Professional allows for a choice between:
1. EPDM login
Users and Groups that are managed through tools and mechanics solely contained within the SOLIDWORKS PDM Application. This may be an ideal choice for smaller user bases with less access, ownership or expertise of server side features.
2. LDAP
Generally, works outside of the Windows structure focusing on the Linux / Unix environment and with more technical applications. LDAP doesn’t have the same concepts of domains or single sign-on. Most used with open source solutions and offers more flexibility. This choice may be best for some companies with very specific requirements and internal specialists to support it.
3. Windows Active Directory (Windows Login)
Primarily a directory for Windows users, devices, and applications requires a Microsoft Domain Controller to be present, and when it is, users can single sign-on to Windows resources that live within the domain structure.
Windows Login Functionality in Solidworks PDM
So you chose Windows Login! SOLIDWORKS PDM Professional can use Windows local or domain account user names and passwords with this setting. When using windows Automatic login, users are logged in automatically without being prompted for their credentials.
Good to Know
- If you choose a PDM Login type, I suggest you mirror your Windows user names for the PDM users. This will let you more easily transition to a windows login type if the need presents itself.
- Passwords will be managed in Windows and not in EPDM.
- The ‘Admin’ login cannot be renamed or linked to a Windows login.
- Only Windows Active Directory Security Groups can be imported and used in SOLIDWORKS Enterprise PDM. Not for example Distribution Groups.
- Any active directory domain group scope can be used when adding domain groups to the SolidWorks Enterprise PDM archive server configuration tool, login settings for Windows logins. This is provided the archive server can access the group.
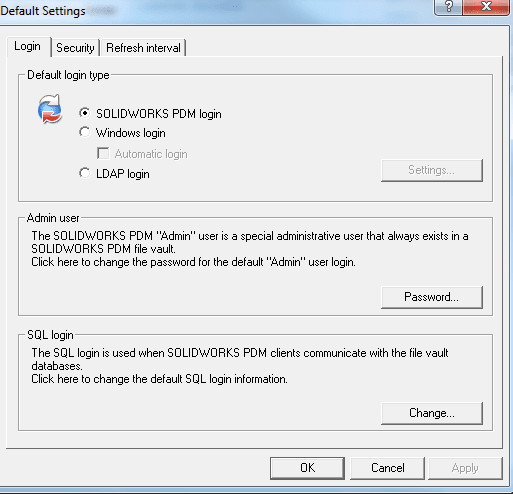
Windows Login Setup
1. Configuring the Active Directory Domain Controller
To create or manage SOLIDWORKS PDM groups using Active Directory, trusted for delegation must be enabled in Active Directory for the archive server computer account.
If the archive server uses Windows login, when the administrator manages users and groups in SOLIDWORKS PDM the archive server queries Active Directory for user and group information. As part of the query, Active Directory does an authentication challenge to ensure that the user has access rights.
For the authentication challenge to succeed when a client is run from a computer other than the archive server, delegation for the archive server computer account in Active Directory must be set to “Trust this computer for delegation.” When Active Directory asks for credentials, this setting lets the archive server computer account forward the client credentials for a user who is logged in to a different computer.
The Active Directory Users and Computers console is required to configure the Active Directory domain controller. Only a domain controller has the Active Directory Users and Computers console installed by default. If the archive server is not a domain controller, you must set up a Microsoft Management Console with the Active Directory Users and Computers snap-in before you perform this procedure.
2. To set delegation to trusted:
Log in to the archive server computer as a member of the Domain Admins group or the Enterprise Admins group in Active Directory.
Click Start > Control Panel > Administrative Tools > Active Directory Users and Computers.
In the Active Directory Users and Computers dialog box, in the left pane, expand the domain controller and locate the computer account for the archive server.
By default, computer accounts are kept in the Computers folder, but they can be in other folders under the domain controller.
In the right pane, right-click the account and click Properties.
On the Delegation tab, select Trust this computer for delegation to any service (Kerberos only).
Click OK.
Close the Active Directory Users and Computers dialog box.
3. Import Groups/Users from the Active Directory
Use the second page of the Import Groups from Active Directory wizard to select individual users for the SOLIDWORKS PDM group.
To display this screen:
Right-click Groups and click Import from Active Directory. Search for Active Directory groups and select those to import. Click Next.
4. Adding Users from Other Domains
To add users from another domain when using Windows® Logins in Enterprise PDM, create a new local Windows group (on the archive server) and add users or groups from the other domain to this local group. Once done, add the local group to the Windows login settings (or attach/administrative access settings) via the archive server configuration tool.
Between domains, the system administrator will create domain trusts. This can be done in one or two ways. The domain A will need to trust the domain where the users are accredited (domain B). Domain administrators on both domains will need to create the trusting relationship (even for a one way trust).
Once the domain trusts are established the following groups will likely be created (may differ depending on Active Directory configuration):
A global group in the trusted domain for adding users, a universal group to which the global group(s) would be added, a domain local group where the resources are located, the universal group would be added to this group.
This provides the links for users from one domain to another.
After the trusts are created it should be possible to create explicit permissions by individual but this is not a recommended practice.
Read more about creating Active Directory domain trusts in the Windows server documentation.
The enquirer should seek the services of a qualified MCSE systems administrator as this is a question of systems administration.
Changing to Windows Login
1. Open the ‘Archive Server Configuration’ tool.
Start > All Programs > SOLIDWORKS Enterprise PDM > Archive Configuration Tool.
2. Right click on the vault you would like to change and choose ‘Properties’.
3. Once in the properties dialog box, uncheck ‘Use default login type’ and select the login type.
‘Windows Login’.
4. This will prompt a second screen (settings) where you will be able to add the various users and/or groups from Windows.
NOTE: when a vault user is not present in the active directory the user icon will show a red plus sign.
5. Open SQL Management Studio, expand the file vault database, expand tables, right click the ‘dbo.users table’ and select ‘edit top 200 rows’.
6. Update the column ‘Username’ to match the Windows Active Directory user names.
NOTE: Do NOT change the users ‘sa’, ‘Admin’ OR ‘<NULL>’
7. Delete any user that had previously shown a red plus sign next to the name should now be removed.
6. Setting up Windows Active Directory User and Computers console on a non domain controller computer.
Windows Server computers
1. Create a Microsoft Management Console with the Active Directory Users and Computers snap-in.
2. Download the Microsoft Windows Server Remote Server Administration Tools which includes the Windows Active Directory User and Computers console.
Windows Workstation computers:
Download the Microsoft Windows Server Remote Server Administration Tools.

 Blog
Blog